Service accounts in Google Cloud are special types of accounts used by applications, virtual machines, and other compute resources to interact with GCP services. Unlike user accounts, service accounts are not tied to human users. Instead, they represent non-human identities with specific roles and permissions, allowing automated processes to securely access cloud resources.
This guide explains the purpose and structure of service-accounts, walks through how to create and manage them using the Google Cloud Console, and provides practical advice on best practices for their use.
The Role of Service Accounts in GCP
Service accounts are used whenever a process or workload, such as a Compute Engine VM, a Cloud Function, or a container in Cloud Run needs to call GCP APIs. Each service account can be assigned one or more IAM roles, defining what the associated workload can do.
They are also used when authentication is needed between services. For example, a VM might use a service account to write logs to Cloud Logging, or a scheduled task might use one to read from BigQuery.
There are three main types of service accounts in GCP:
- User-managed service accounts: Created and managed by project users.
- Default service accounts: Automatically created by GCP when certain services (like Compute Engine) are enabled.
- Google-managed service accounts: Used internally by GCP services; these are generally not directly managed by users.
Creating a New Service Account
Creating a service account is often the first step when setting up automation or inter-service communication.
In the GCP Console, navigate to IAM & Admin.
Then select Service Accounts.
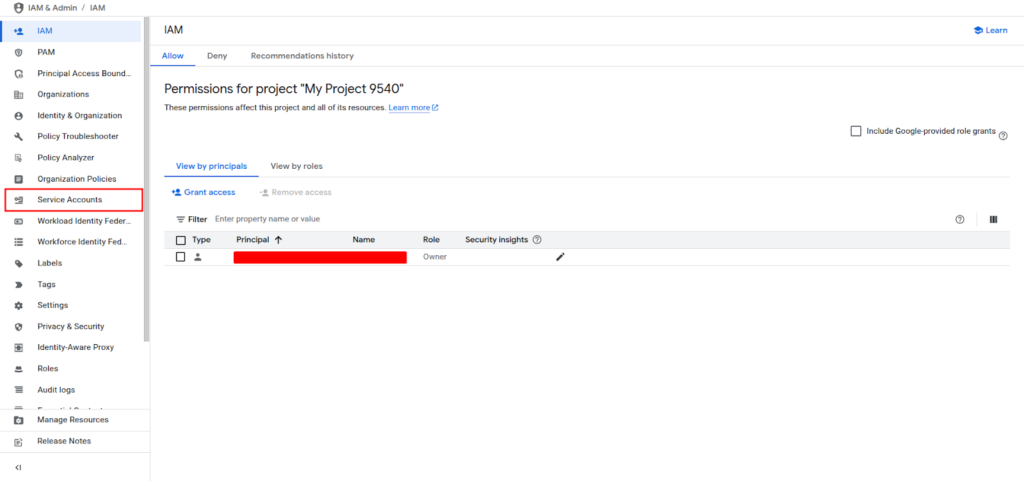
Click “Create Service Account.”
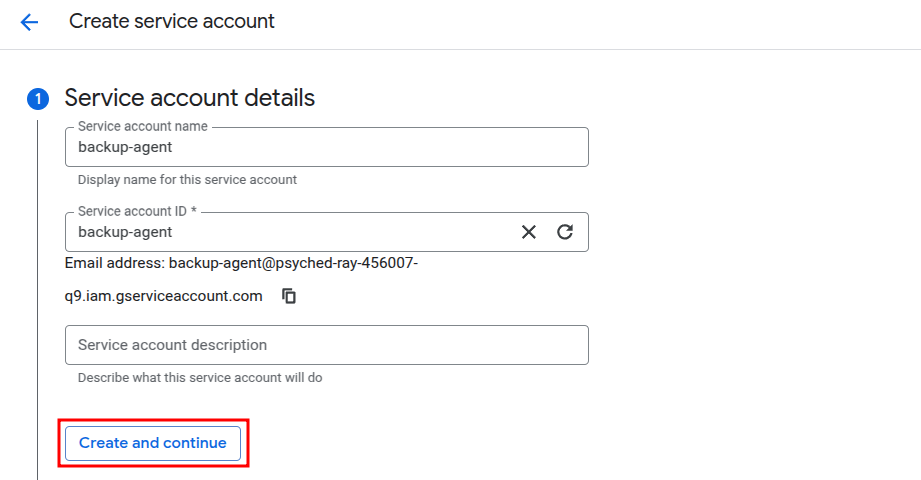
Provide a name and ID for the service account. This name will help identify its purpose, such as backup-agent or report-generator.
In the next step, assign one or more roles to the service account. For instance, a backup agent may require access to read from Compute Engine and write to Cloud Storage. Selecting roles at this stage defines the permissions available to any process that uses this account.
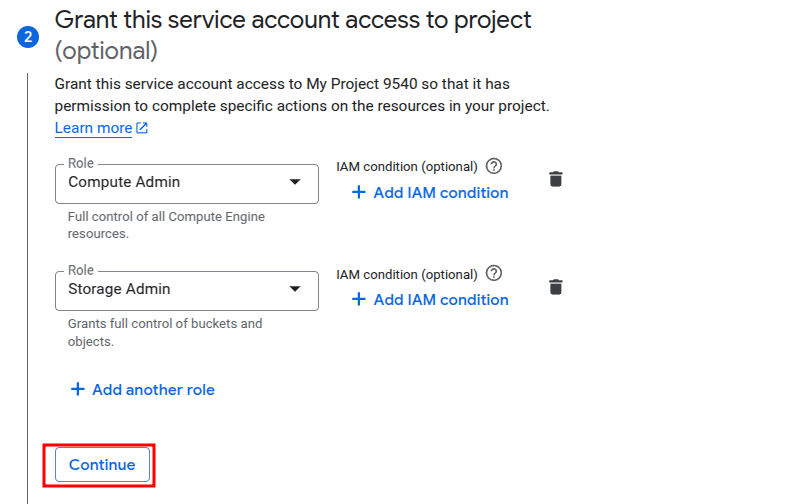
After reviewing the configuration, click “Done” to finish the creation.
The new service account will now appear in the list and can be used with compute resources or automated workflows. For demonstration purposes, permissions were not filtered during role creation; in real-world scenarios, always review and select only the necessary permissions to adhere to the principle of least privilege.
Generating and Managing Keys
In some cases, external applications need to authenticate to GCP using service accounts. This is done using a key file, typically in JSON format.
To generate a key, go to the Service Accounts page, and select the account.
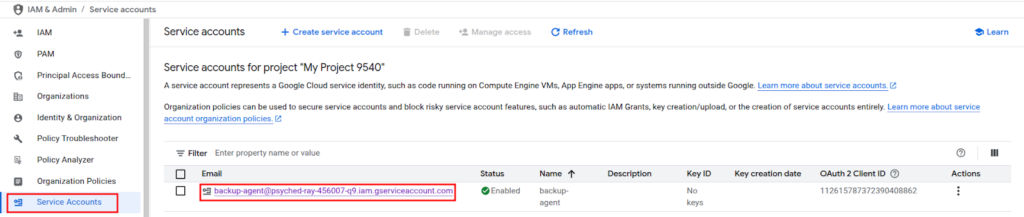
Then open the “Keys” tab. Click “Add Key” and select “Create new key.”
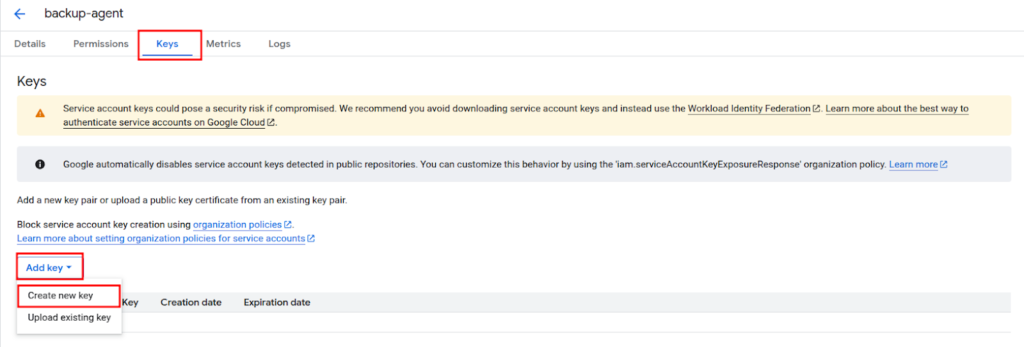
Choose JSON as the format.
Download the key file when prompted
This key allows external applications to authenticate as the service account and perform actions according to its roles. It is important to secure this key file, as it grants access to GCP resources.
Keys should be stored securely, rotated regularly, and never hardcoded or exposed in version control. If a key is compromised, it should be deleted immediately from the console to prevent misuse.
Assigning Service Accounts to Compute Resources
When deploying workloads on GCP, it is possible to attach a service account to the resource, allowing it to inherit the permissions of that account.
For example, when launching a new Compute Engine instance, the service account can be selected during the setup process. The instance will use that account to make authenticated API calls.
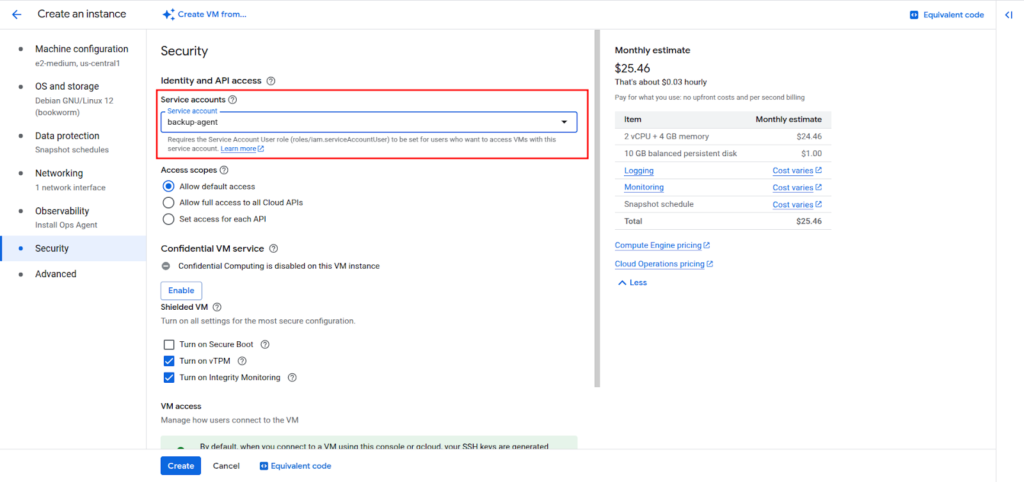
Similarly, services such as Cloud Run, Cloud Functions, and Dataflow support specifying a service account under their configuration settings.
Attaching the correct service account ensures that the workload can access necessary resources without over-privileging or relying on user credentials.
Auditing and Monitoring Service Account Usage
To maintain a secure environment, it is important to monitor how service accounts are being used.
In the GCP Console, the Logs Explorer under Operations > Logging can be used to view activity from service accounts. Filtering logs by service account email or by relevant services (such as IAM, Compute Engine, or Cloud Storage) provides visibility into which operations were performed and when.
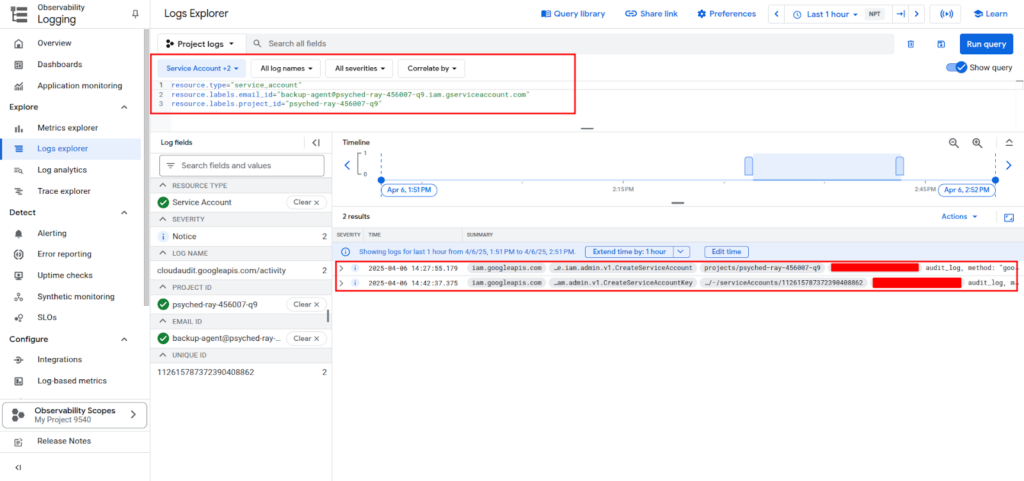
Reviewing audit logs regularly helps detect unauthorized usage or misconfigured permissions. Logging is especially important for service accounts with high privileges or used by critical applications.
Best Practices for Service Accounts
- Use a dedicated service account for each workload or application to isolate permissions.
- Assign only the roles necessary for the task at hand to follow the principle of least privilege.
- Rotate service account keys regularly and store them securely, preferably in a secret manager.
- Avoid using default service accounts in production environments, as they often have broad permissions.
- Audit service account usage periodically using logs and IAM policy analysis.
Service Accounts in GCP
Over-provisioned access can lead to compliance risks and resource waste. Elite Cloud helps configure service accounts to minimize exposure while reducing unnecessary IAM-related costs.
Contact us to tighten permissions and cut hidden access expenses.
Conclusion
Service accounts are a foundational component of secure automation and inter-service communication in Google Cloud. By understanding how they work, creating and managing them properly, and following best practices, teams can build cloud applications that are both powerful and secure.
Using the console provides an intuitive way to manage service accounts, define their roles, generate secure credentials, and monitor their usage. For more advanced environments, these practices can be integrated into infrastructure automation using tools like Terraform or the gcloud CLI.
FAQs
What are Service Accounts in GCP used for?
Service Accounts in GCP let applications or virtual machines interact with Google Cloud securely. They’re non-human accounts that help automate tasks by giving just the right permissions.
How do I create a new service account?
In the GCP Console, go to IAM & Admin, choose Service Accounts, then click “Create Service Account.” Add a name and assign roles depending on the job it needs to perform.
What are the different types of service accounts?
There are three types: user-managed, default (auto-created), and Google-managed. User-managed accounts offer full control, while Google-managed ones are handled internally.
How do service account keys work?
Keys are JSON files used by external apps to authenticate. They must be stored securely and rotated regularly to prevent unauthorized access to GCP services.
Can I monitor how service accounts are used?
Yes, you can use Logs Explorer in GCP to track actions made through service-accounts. Regular auditing helps detect misconfigurations or unauthorized activity.




