In modern cloud environments, controlling access to resources securely and efficiently is critical. Google Cloud IAP as a robust solution to manage access based on user identity and context. Whether it’s web applications, APIs, or virtual machines, IAP enables organizations to enforce access policies without relying on traditional network-level protections like VPNs or public IPs.
In this article, we’ll provide an overview of GCP IAP, its components, use cases, and how it strengthens your cloud security model. Then, we’ll walk through a practical implementation: using IAP to access a virtual machine instance.
What is Google Cloud IAP?
Identity-Aware Proxy (IAP) is a service that controls access to cloud resources by verifying the identity of a user and the context of their request. Instead of relying on network-based firewalls or perimeter security, IAP enforces policies based on Google Cloud IAM roles and conditions.
IAP provides access control for:
- Web applications deployed on App Engine, Cloud Run, or Compute Engine
- HTTP/HTTPS services behind a load balancer
- SSH and RDP access to virtual machines
- Internal tools and APIs
Google Cloud IAP Core Features
Identity-Based Access
IAP ensures that only authenticated and authorized users can access protected resources. It leverages Google Workspace identities or Cloud Identity and integrates tightly with Cloud IAM for fine-grained control.
Context-Aware Access
Policies can incorporate additional context, such as device security status, IP location, or user attributes, enabling adaptive access control.
Logging and Auditing
All access attempts and actions are recorded in Cloud Audit Logs, making it easy to monitor usage and detect suspicious activity.
No Public Exposure Required
Resources protected by IAP can be kept completely private, without public IP addresses or exposed ports.
Common Use Cases
- Restricting access to internal web applications
- Protecting custom APIs with identity verification
- Enabling secure access to VMs for developers and administrators
- Replacing bastion hosts or VPNs with a simpler, identity-driven model
Implementation Focus: Using IAP to Access a Virtual Machine
For this article, we will focus on how IAP can be used to securely access a virtual machine instance over SSH. This use case is ideal for organizations looking to minimize their attack surface while maintaining convenient access for authorized personnel.
By the end of the guide, you’ll be able to:
- Set up a VM without a public IP
- Configure IAM roles for IAP access
- Use the Google Cloud Console to connect to the VM over IAP
Step-by-Step Guide: Accessing a VM with IAP over SSH
In this example, we’ll demonstrate how to configure and use IAP to securely SSH into a VM instance that does not have a public IP using the Google Cloud Console.
Prerequisites
Before we begin, ensure you have the following:
- A Google Cloud project with billing enabled
- A Compute Engine VM instance (can be newly created or existing)
- Your user account has the necessary IAM permissions:
- roles/iap.tunnelResourceAccessor (for IAP TCP tunneling)
- roles/compute.instanceAdmin.v1 (for VM access)
- roles/compute.osLogin (if OS Login is enabled)
Step 1: Create a VM Without a Public IP
Go to the Compute Engine then select VM instances page in the Google Cloud Console.
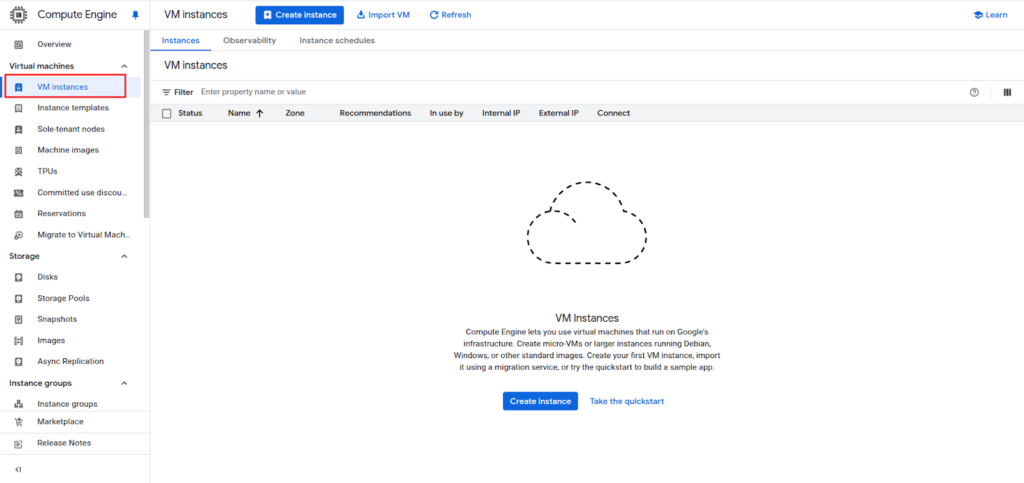
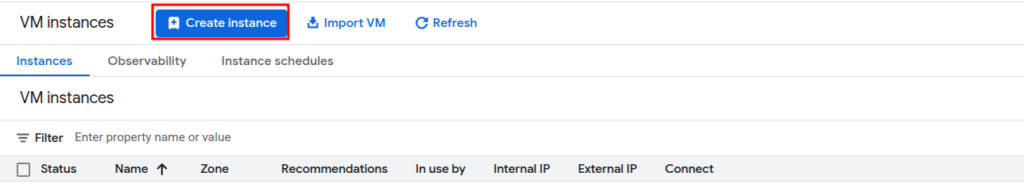
Click Create Instance.
In the “Networking” section, under “Network interfaces,” choose None for External IP.
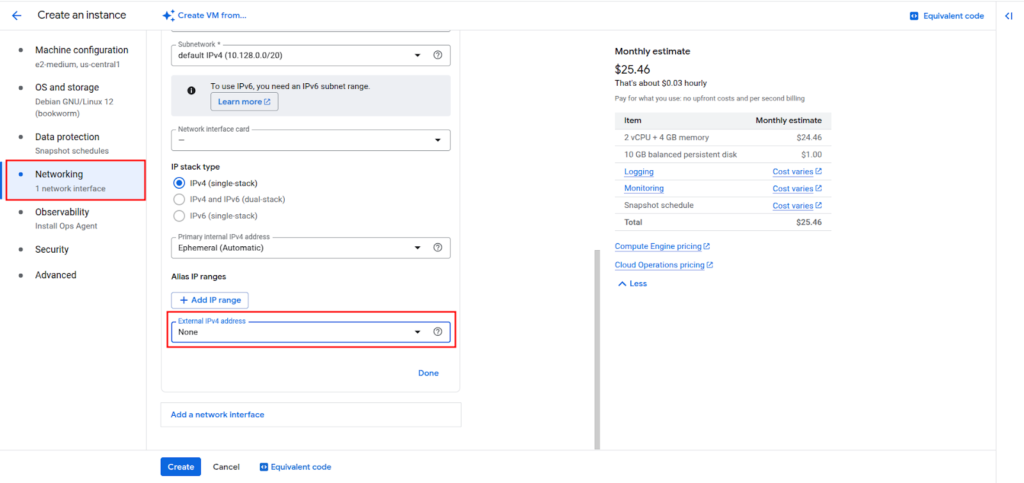
This ensures the VM has no public IP and can only be accessed through IAP. Then create the VM.
Step 2: Enable IAP and OS Login
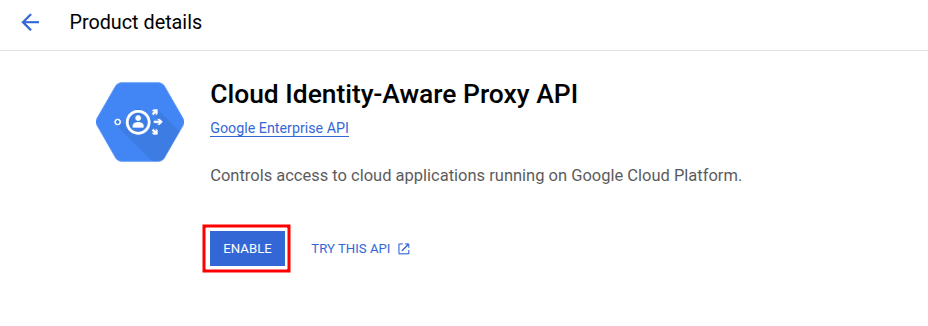
Navigate to APIs & Services then select Library.
Search and enable the Identity-Aware Proxy API.
OS Login allows you to manage SSH access to your VM instances using IAM roles rather than manually configured SSH keys. It creates a Linux user account based on your Google identity and provisions SSH keys automatically when you connect. This approach simplifies access management, enhances security through centralized control, and enables better auditing since all access is tied to specific user identities.
1. Go to Compute Engine > Metadata.
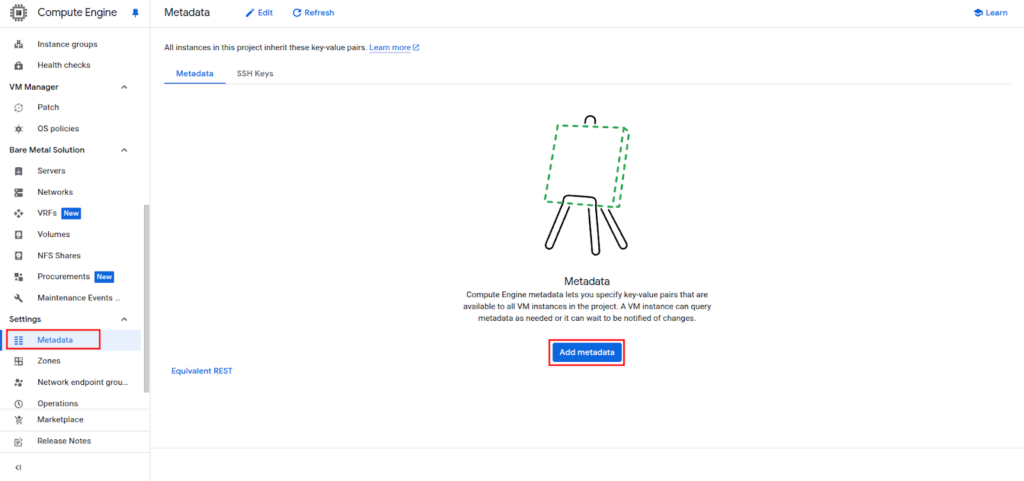
2. Click Add metadata. Add the metadata key enable-oslogin with the value TRUE.
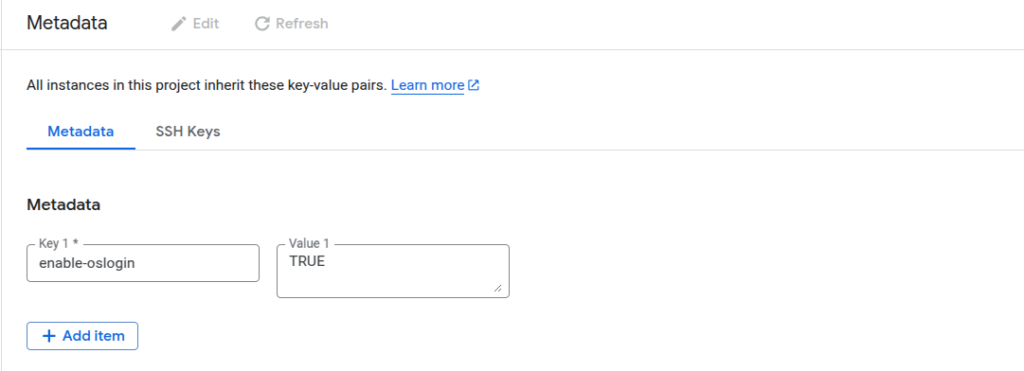
Save changes.
You can also enable OS Login at the instance level by editing the instance metadata.
Step 3: Assign IAM Roles
Go to IAM & Admin > IAM and grant the following roles to your user or group:
- IAP-secured Tunnel User
- Compute Instance Admin (v1)
- Compute OS Login
You can do this by clicking Grant Access, entering the email, and selecting the roles.
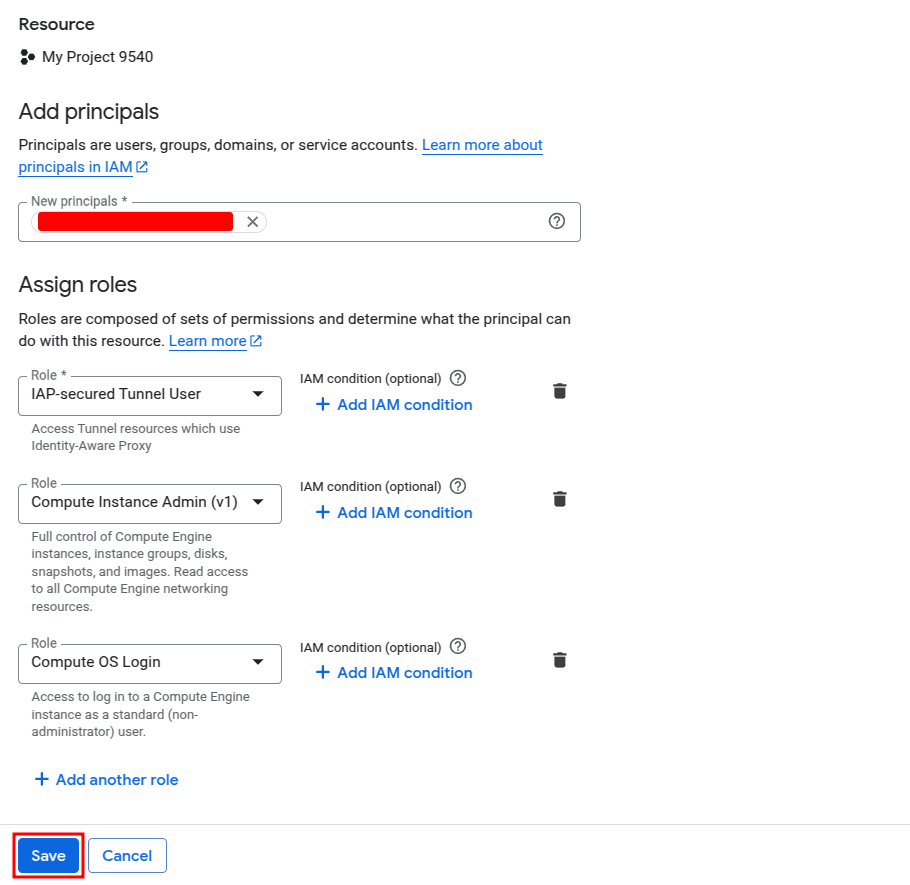
Step 4: Connect to the VM via IAP
Return to Compute Engine > VM instances. Find your VM and click the SSH button under the “Connect” column.
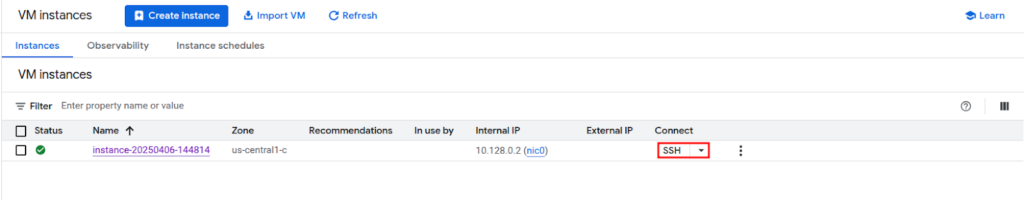
This automatically establishes an SSH session through IAP without requiring an external IP.
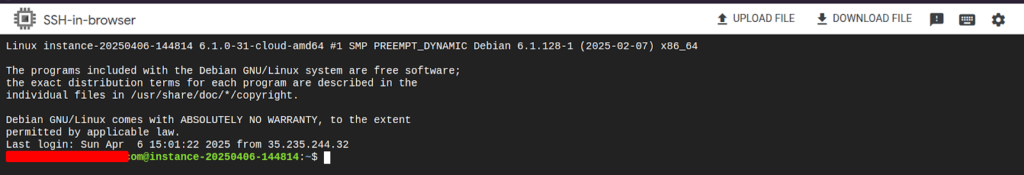
Step 5: Verify Access and Logs
To audit access:
Go to Logging > Logs Explorer.
Now use the query: iap.googleapis.com to filter IAP tunnel logs.
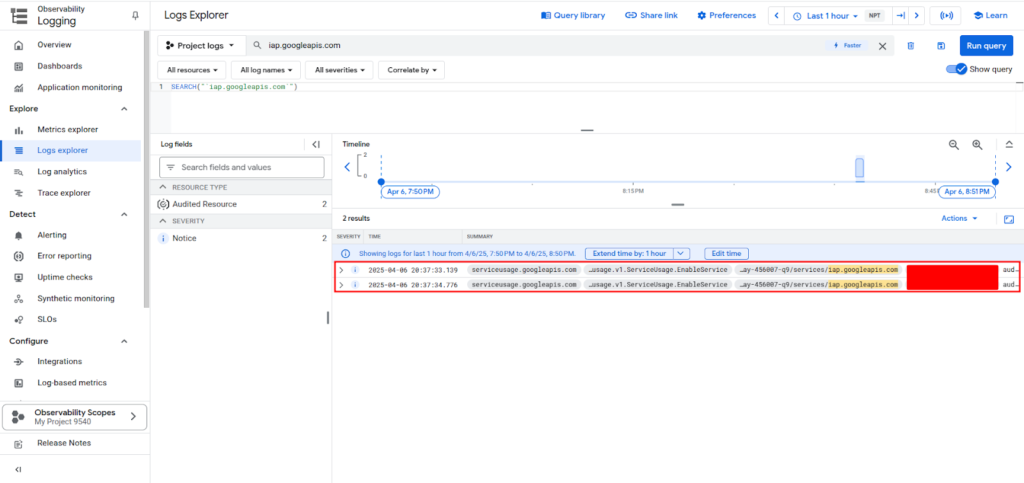
This will show access events, IPs, user IDs, and timestamps.
Recap
By using IAP for VM access, you:
- Avoid exposing your VMs to the public internet
- Simplify access control with IAM roles
- Gain visibility through centralized logging
- Eliminate the need for bastion hosts or VPNs
This approach aligns with the zero-trust security model, which is increasingly becoming the standard for secure cloud operations.
Google Cloud IAP
Eliminate the cost of maintaining VPNs, bastion hosts, and firewall configs. With Google Cloud IAP, Elite Cloud helps you streamline secure access while lowering operational overhead.
Talk to us about simplifying access and saving infrastructure costs.
Conclusion
Google Cloud’s Identity-Aware Proxy (IAP) provides a modern, identity-centric approach to securing access to cloud resources. By eliminating the need for traditional bastion hosts, public IP addresses, or VPNs, IAP significantly reduces the attack surface while improving access manageability and auditing capabilities. Implementing IAP for VM access as demonstrated in this guide helps enforce security best practices and supports compliance in multi-user environments. As cloud infrastructure continues to grow in complexity, tools like IAP are essential for maintaining a secure and scalable access strategy.
FAQs
What is Google Cloud IAP used for?
Google Cloud IAP helps control access to apps, VMs, and APIs based on user identity and context. It replaces VPNs and public IPs with identity-based access control.
Can I use Google Cloud IAP to access VMs without a public IP?
Yes, IAP allows you to SSH into VMs that have no external IPs, reducing your cloud infrastructure’s exposure to threats while maintaining secure access.
What roles are needed to access a VM via Google Cloud IAP?
You’ll need roles like IAP-secured Tunnel User, Compute Instance Admin (v1), and Compute OS Login. These control SSH access and tunnel authorization.
How does Google Cloud IAP enhance security?
It eliminates the need for bastion hosts and uses centralized identity policies. You also get detailed audit logs for every access event.
Is OS Login required with Google Cloud IAP?
While optional, enabling OS Login simplifies account management by linking SSH access to Google identities, enhancing both security and user traceability.




