In today’s digital landscape, protecting your workloads from advanced threats is more critical than ever. With 17% of cloud breaches linked to vulnerable configurations, ensuring robust security for your virtual machines is a top priority. GCP Shielded VMs offers a solution designed to safeguard your environment against risks like rootkits and bootkits.
One common issue many face is SSH connection errors after resizing instances. These errors can disrupt operations and expose vulnerabilities. By leveraging features like vTPM, Secure Boot, and Integrity Monitoring, you can minimize such risks and maintain a secure infrastructure.
What Are Shielded VMs?
Shielded VMs are virtual machines that leverage advanced security features to safeguard against rootkits, bootkits, and unauthorized changes. They provide:
- Secure Boot: Ensures only trusted, signed operating system images are loaded.
- Virtual Trusted Platform Module (vTPM): Enables cryptographic integrity checking and disk encryption.
- Measured Boot: Records boot measurements and verifies against a baseline.
- Integrity Monitoring: Alerts administrators if unexpected changes occur.
How to Enable GCP Shielded VMs
To enhance your cloud security, enabling advanced protections is a must. These features safeguard your instances from sophisticated threats. You can activate them using either the console or the command-line interface (CLI). Both methods are straightforward and effective.
Let’s go step by step to create and configure a Shielded VM.
Step 1: Log in to Google Cloud Console
1. Navigate to Google Cloud Console.
2. Ensure you have an active billing account and a project set up.
Step 2: Enable Required APIs
Before creating a Shielded VM, ensure that the Compute Engine API is enabled.
1. Go to APIs & Services then click on Library.
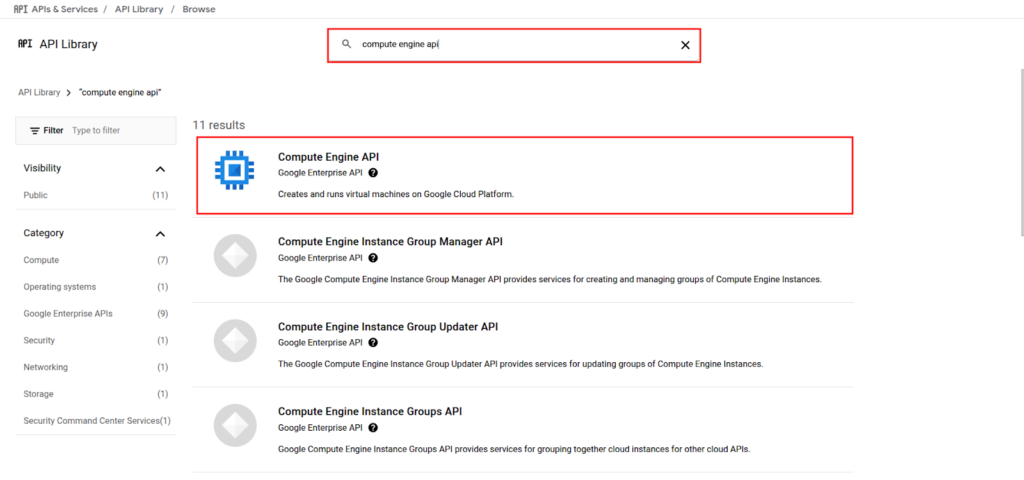
2. Search for Compute Engine API.
3. Click Enable if it’s not already enabled.
Step 3: Create a Shielded VM Instance
1. Navigate to Compute Engine > VM instances.
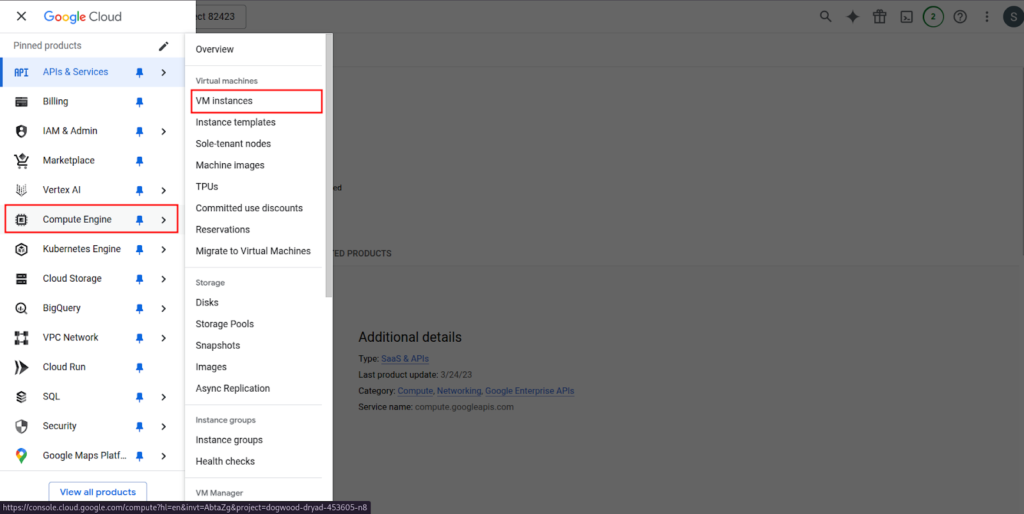
2. Click Create Instance.
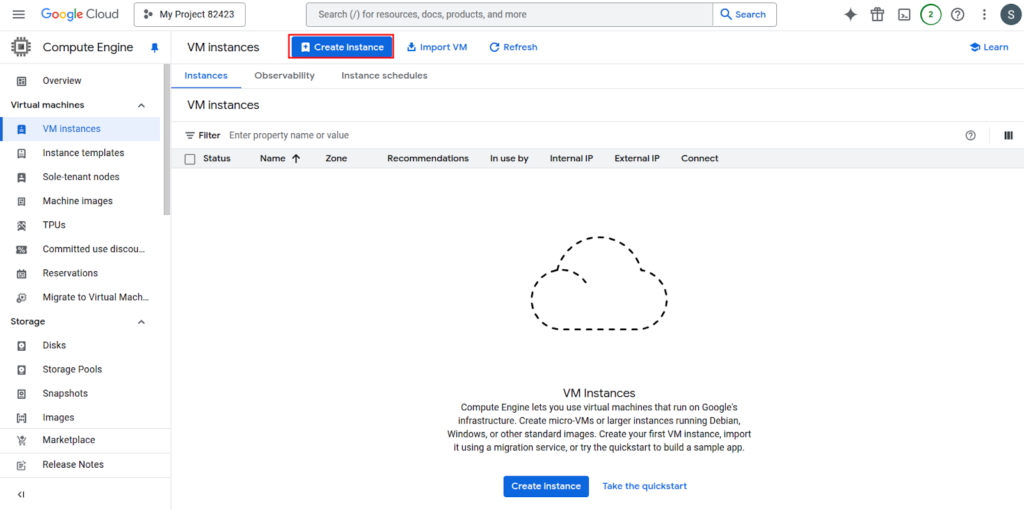
3. Configure the following:
- Name: Enter a unique name for your VM.

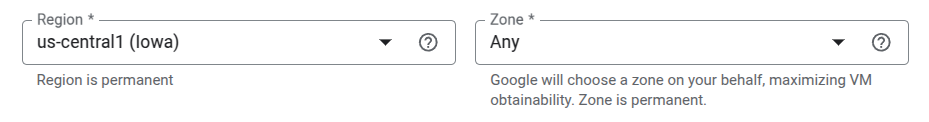
Region & Zone: Select a location based on your needs.
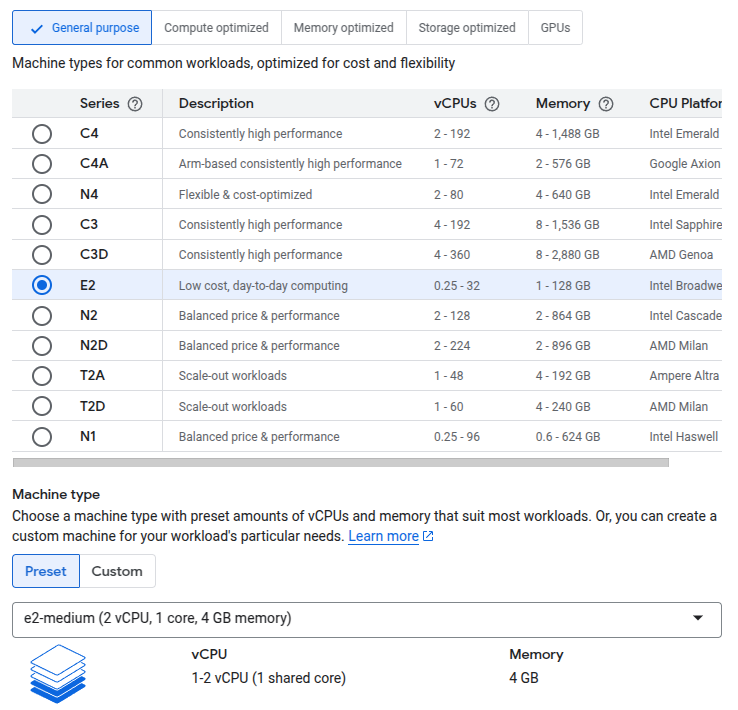
Machine Type: Choose the required CPU and memory.
Boot Disk: Click Change and select a Shielded VM-supported OS (e.g., Debian, Ubuntu, Windows Server).
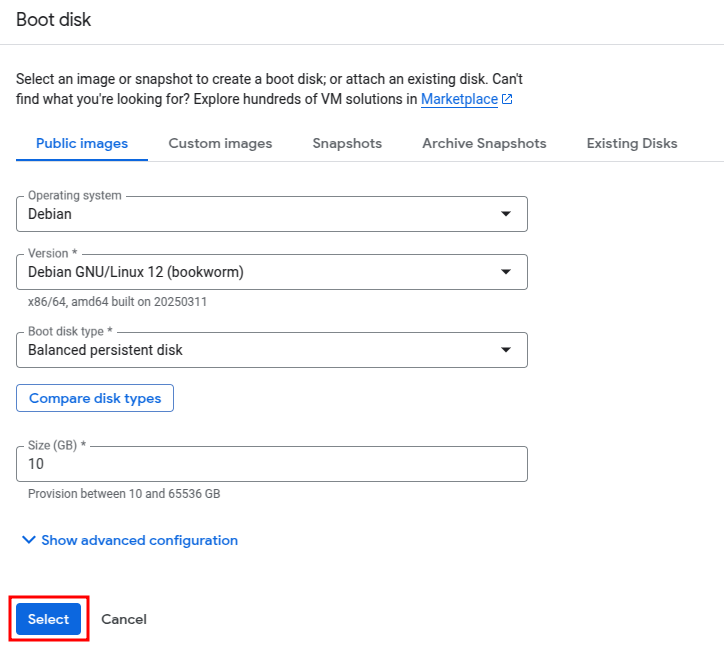
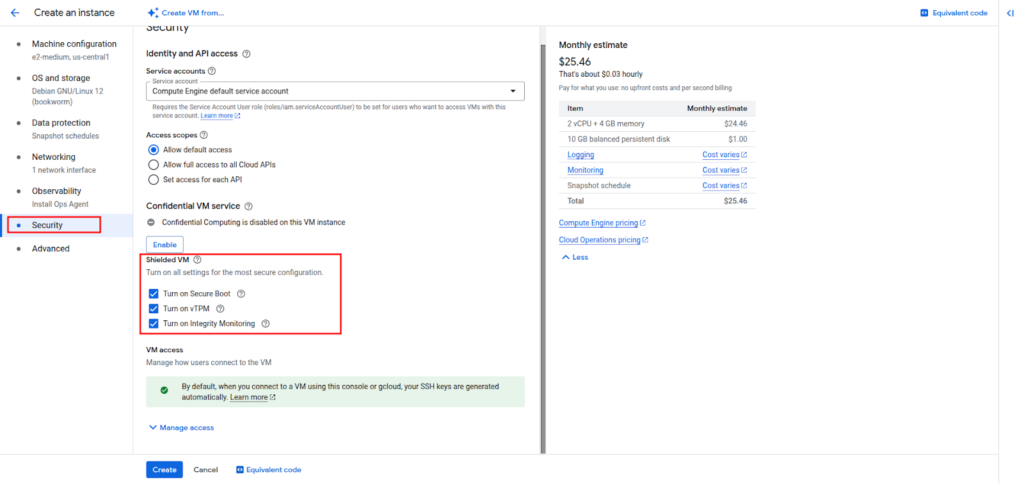
Step 4: Enable Shielded VM Features
Scroll down to the Security section and ensure the following options are enabled:
- Secure Boot
- vTPM
- Integrity Monitoring
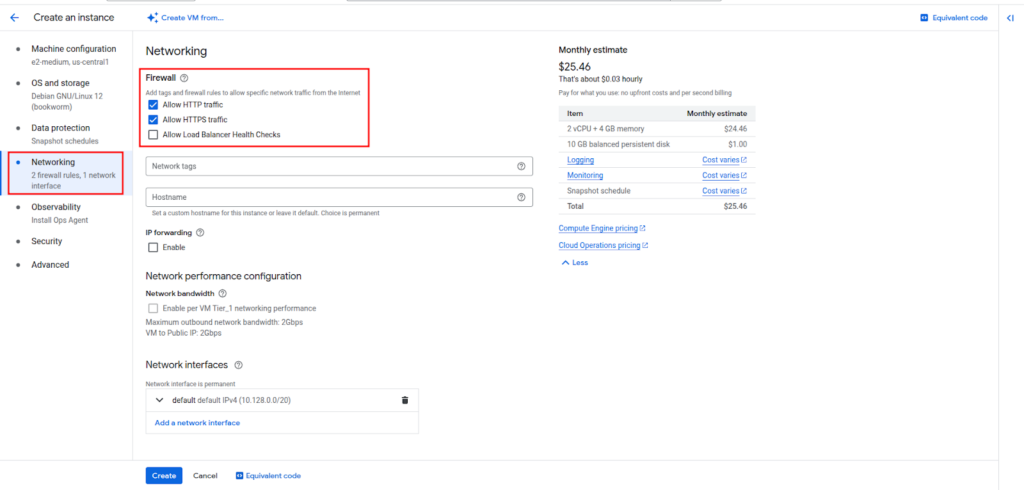
Step 5: Configure Firewall and Networking
- Check Allow HTTP and HTTPS traffic from the networking tab, if you plan to host web services.
- Optionally, set up custom firewall rules.
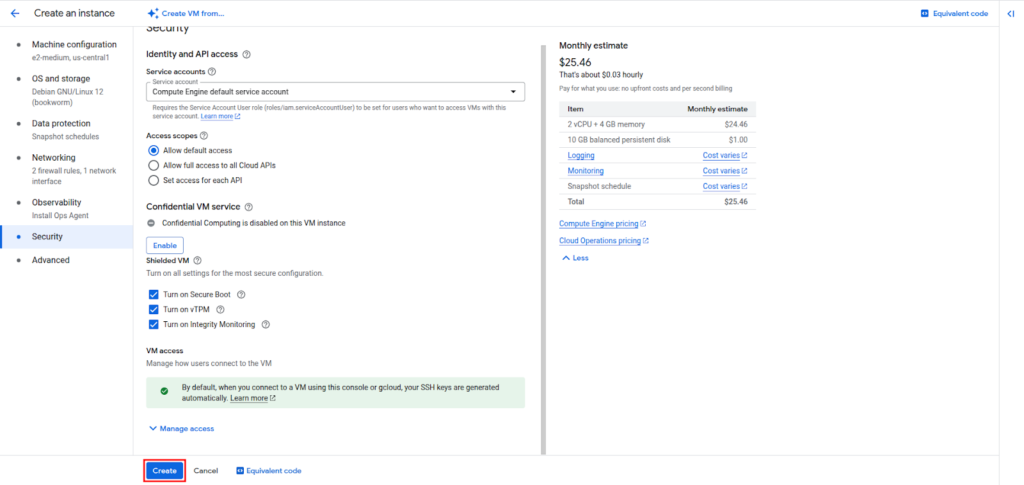
Step 6: Create the VM
1. Click Create and wait for the instance to start.
2. Once running, click SSH to connect to your VM and verify settings.
Step 7: Verify GCP Shielded VMs Features
Run the following command inside your VM to install the tmp utilities: `sudo apt install -y tpm2-tools`
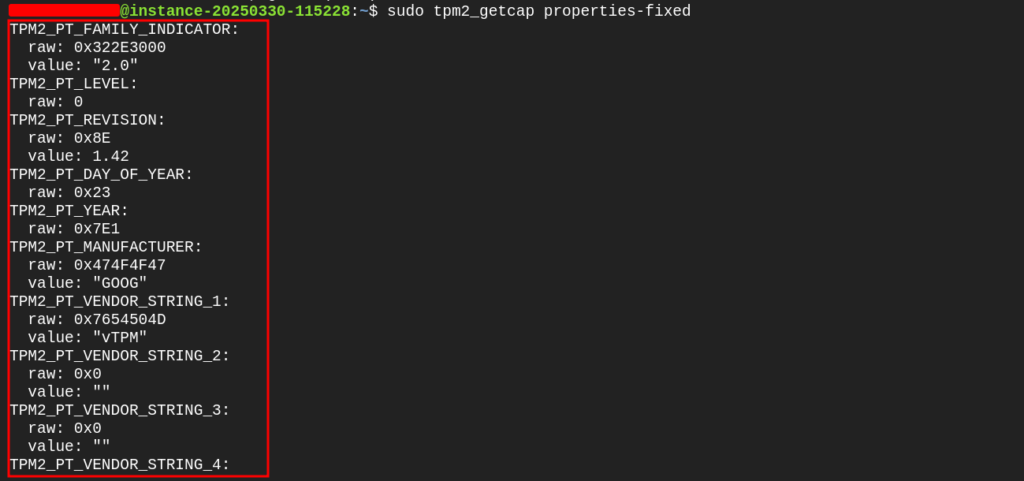
To confirm that vTPM is enabled run the command `sudo tpm2_getcap properties-fixed`
Conclusion
Securing your cloud environment demands a proactive approach to advanced protections. By leveraging the three-layer protection matrix—vTPM, Secure Boot, and Integrity Monitoring—you can safeguard your workloads from sophisticated threats. Always follow best practices for resize operations to avoid disruptions and maintain system integrity.
Be cautious with Marketplace images, as they may not support all advanced features. Regularly update your baseline policies post-configuration to stay ahead of emerging threats. Finally, keep an eye on upcoming features like runtime memory encryption to further enhance your security posture.
Protect your workloads with GCP Shielded VMs
Elite Cloud helps you deploy and manage Shielded VMs with:
- Verified boot and vTPM for rootkit protection
- Integrity monitoring to detect unauthorized changes
- OS policy hardening for secure, compliant environments
📞 Talk to an expert now and secure your infrastructure with confidence.
FAQ
What are the key security features of GCP Shielded VMs?
Shielded VMs offer secure boot, virtual trusted platform module (vTPM), and integrity monitoring to protect your workloads from threats like bootkits and rootkits.
How do I enable GCP Shielded VMs on my instances?
You can enable Shielded VMs using the Google Cloud Console or the gcloud CLI by selecting the appropriate options during instance creation or modification.
What is the role of the virtual trusted platform module (vTPM)?
The vTPM provides secure storage for encryption keys and ensures the integrity of the boot process, safeguarding your data from unauthorized access.
Can I enable Shielded VMs features on existing instances?
Yes, you can edit your existing instances to enable Shielded VM features through the Google Cloud Console or CLI.
How does integrity monitoring enhance security?
Integrity monitoring continuously checks the boot process and system files for unauthorized changes, helping you detect and respond to potential threats quickly.
Are GCP Shielded VMs compatible with all machine images?
Shielded VMs work with most public images and custom images that meet the necessary requirements. Check the Google Cloud documentation for a detailed list of supported images.
What are the benefits of using secure boot?
Secure boot ensures that only verified and signed software can run during the boot process, preventing malicious code from compromising your system.
How do I verify if GCP Shielded VMs features are active on my instance?
You can check the status of Shielded VM features in the instance details section of the Google Cloud Console or by using the gcloud CLI.




